Now Reading: Web3 Security in 2026: The “Audit-Only” Era is Dead
-
01
Web3 Security in 2026: The “Audit-Only” Era is Dead

Web3 Security in 2026: The “Audit-Only” Era is Dead
- The crypto industry suffered a record-breaking $3.4 billion in losses in 2025. This figure includes the massive $1.5 billion Bybit breach.
- A new report by security firm Sherlock signals the end of the “audit-only” era. The focus is moving toward operational security and internal controls.
- Discussions on r/web3 highlight that attackers now target infrastructure and human error rather than code vulnerabilities.
- Supply chain attacks, address poisoning, and private key management failures are replacing simple smart contract exploits as primary risks.
If 2025 was the year of the $3.4 billion wake-up call, 2026 is shaping up to be the year the battlefield shifts entirely. After a record-breaking year of losses led by the $1.5 billion Bybit breach, security experts and the broader Web3 community are signaling the end of the audit-only era. The industry narrative is changing fast. Simple smart contract exploits are no longer the main threat. A deeper layer of systemic and operational risk is taking center stage.
The $3.4 Billion Lesson
According to a new report by security firm Sherlock, losses in 2025 were not driven by scattered bugs but by a concentration of large-scale failures. The report highlights how risk now accumulates faster than most teams can respond. It also points out that many affected projects were not careless or ignored best practices. Instead, attackers consistently found weaknesses in areas that traditional security programs were never designed to defend.
Looking into 2026, Sherlock expects protocols to stop accepting partial security assurances. Simply pointing to a completed audit is losing credibility. More attention is shifting toward operational security. This includes key custody, upgrade governance, infrastructure controls, internal access management, and third-party dependencies.
Community Debate
This evolving mindset is also reflected in a recent discussion on the r/web3 subreddit, where a thread posted by SolidityScan asked the community to predict how Web3 hacks will change in 2026. The post highlighted how 2025 marked a visible shift away from smart contract-only exploits toward access control failures, infrastructure breaches, and operational breakdowns.
Several responses from the thread are gaining traction and shaping the wider conversation. One highly discussed reply argued that total losses are unlikely to drop in 2026, even if the nature of attacks changes.
“I doubt total losses go down in 2026. The shape definitely changes, though. Smart contract exploits feel more known knowns now. Audits, formal verification, bug bounties are better. Attackers are already shifting to keys, infra, CI CD pipelines, RPCs, bridges, and governance capture. Humans and ops stay the weakest link.”
Another widely shared response pointed to quantum-related risk. While not an immediate threat, the argument was that it already affects how the industry should think about long-lived keys and custody strategies. The concern is not necessarily more frequent exploits, but a larger blast radius when failures occur.
Where Attacks Are Headed Next
Address-related scams also featured heavily in the discussion. Several community members warned about the continued rise of address spoofing and poisoning attacks. These scams rely on generating wallet addresses that closely resemble trusted contacts. While naming services such as blockchain domain systems can reduce this risk, adoption remains uneven. The result is a steady stream of silent losses that rarely make headlines but collectively drain millions from everyday users.
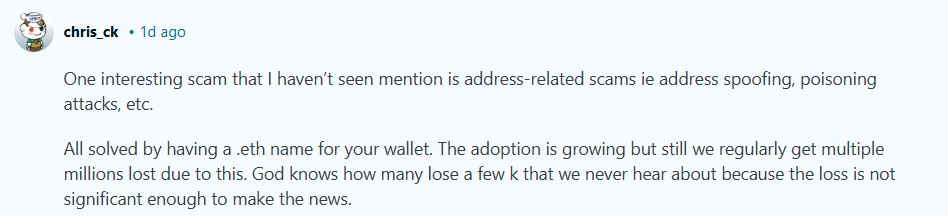
Another response that resonated strongly across the thread summarized the situation in simple terms. The problem in 2026 is not the code. It is the people and the process. Attackers have learned that tricking a human or stealing credentials is far easier than finding a critical flaw in a mature smart contract.
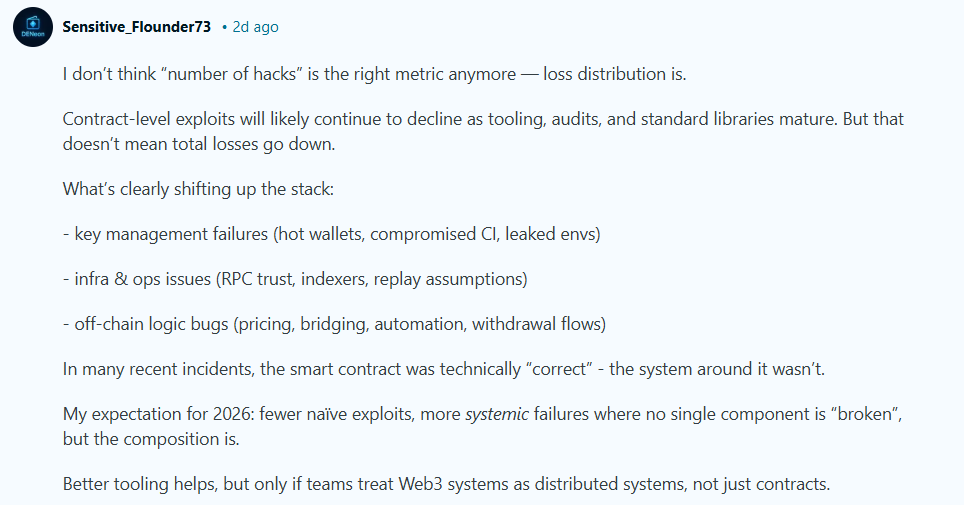
More technical voices in the discussion emphasized that the number of hacks is becoming a less meaningful metric. Instead, the focus is shifting toward loss distribution. Contract-level exploits are expected to decline as tooling and standards mature. At the same time, failures related to key management, infrastructure assumptions, off-chain logic, automation systems, and bridging mechanisms are becoming more common. In many recent incidents, contracts were technically correct. The surrounding system was not.
Supply Chains, Privacy, and the AI Debate
Supply chain attacks also emerged as a major concern. Several participants pointed to recent compromises of trusted interfaces and tooling, suggesting that dApp front ends and developer dependencies may become prime targets. The consensus was that awareness alone would not prevent these incidents. Structural changes in how software is built and deployed will be required.
“Supply chain hacks for dapps. Safe and Trust (irony with their names) hacks were both done this way. Tooling and awareness won’t help.”
Privacy-related attack vectors were also raised. Some community members speculated that exposing user identities tied to transactions originally intended to remain private could become a new attack pattern in 2026 and beyond.
On the tooling front, the thread starter acknowledged that AI-based security tools could help reduce risk. However, others pushed back, warning that large-scale automated monitoring comes with serious trade-offs. Scanning every operational action introduces high compute costs, slower workflows, and new privacy concerns.
Editorial Note: This news article has been written with assistance from AI. Edited & fact-checked by the Editorial Team.
Interested in advertising with CIM? Talk to us!







